Key Takeaways
- Constraints such as tight budgets, increased responsibilities, lack of resources or incentive, and disagreement on a common approach to information security pose challenges for higher education IT organizations wanting to establish a comprehensive information security program.
- An iterative approach to a security program takes advantage of regular audits to find problems and address them according to risk and priority of each lapse identified.
- The IT organization's security program gets stronger with every audit cycle, and the approach provides a good basis for comparing past performance and measuring progress.
Digitization of information assets has allowed organizations to easily store and readily share information. But the same phenomenon has also made these information assets vulnerable to security breaches. The need to protect data and comply with federal laws and regulations such as FERPA, HIPAA, GLBA, PCI DSS, etc., has created several challenges for higher education IT.
To meet these challenges, many higher education IT institutions go through internal or external security audits that produce audit findings. An audit finding represents a failure of existing security controls or points to lack of enforcement of existing policies. Most IT organizations would prefer to put together a comprehensive information security program to prevent these failures from occurring in the first place. Despite their best efforts some organizations are unable to do so due to constraints such as:
- Shrinking budgets and increased responsibilities
- Lack of security focus due to the absence of a dedicated security team
- Lack of resources or staff for an existing security team
- Lack of a common approach to information security
Given these constraints, this article proposes an approach to incrementally building a security program. The examples presented in this article are not intended to be prescriptive, but only to clarify the approach.
Approach in Brief
An IT organization can implement an information security program in four steps:
- Identify an information security framework/standard that will be the basis of the security program.
- Perform a security audit.
- Review the audit findings in the context of the selected framework/standard.
- Identify risk levels and establish a priority for developing policies, procedures, and controls.
The first step is performed during the first iteration; the last three steps are repeated in a continual loop (see figure 1). The approach is iterative in nature and allows an organization to incrementally build a security program using a risk-based approach to implementation.
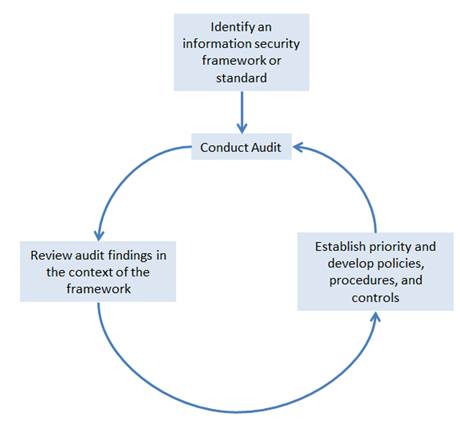
Figure 1. Approach for incrementally building a security program
Step 1: Identify an Information Security Framework/Standard
Using a framework/standard has two distinct advantages:
- A framework/standard represents the collective wisdom of other organizations that have implemented security programs. Even if the industry framework/standard does not fit an IT organization, it can always form the basis of a version tailored for that organization.
- Adopting a framework/standard promotes a common security vocabulary and a common understanding of security throughout the IT organization, which can lead to greater collaboration and better communication.
Several frameworks/standards are available for information security, including:
- NIST 800 series publications1
- ISO 27001
- COBIT Information Security
- ITIL
These frameworks/standards provide guidance on the key elements of a security program:
- Governance
- Policies
- Risk management
- Training and awareness
- Security controls
- Ongoing monitoring
Some frameworks/standards describe information security more extensively than others. Organizations can study the framework/standards and pick one as the primary security standard for the institution. An organization can also combine the best practices from multiple frameworks/standards to create a tailored standard for its needs. For example:
While ITIL provides broad guidelines on how an Information Security Management program should be structured, it leaves the choice of the security control framework to the organization. The organization can choose to implement security controls based on ISO 27001.3
For the purpose of this article I restrict the discussion to governance, policies, risk management, security controls, and ongoing monitoring and explore how an organization can implement these once a standard is chosen. Training and awareness exceed the focus of this article, although they are important to acceptance of and compliance with an information security program.
Let's assume that an organization chooses NIST publications for guidance, specifically, NIST-800-53 for security controls and NIST 800-100 for a broad overview of the security program elements and guidance on governance.2
Step 2: Conduct Audit
Once a framework/standard is selected, an organization can perform an internal or external security audit.
Step 3: Review the Audit Findings
By reviewing the audit findings within the context of a framework/standard, an IT organization can address the following elements of a security program:
- Governance
- Security controls
Governance
To address audit issues, most organizations form teams and make specific assignments. The organization can use the NIST-800-100 publication as a reference to develop and codify some of the team's roles and responsibilities. This is especially handy when there is no formal security governance structure in place.
Note: Even though the NIST-800-100 publication is geared toward the federal government, it is a valuable resource for a list of security personnel, roles, and responsibilities. COBIT Information Security also provides good generic guidance on organizational structure and roles and responsibilities.
Security Controls
NIST describes security controls as safeguards and countermeasures that are specified for information systems. It groups related security controls into categories called security control families. Some examples of control families are Access Control, Identification and Authentication, Media Protection, Personnel Security, and System and Services Acquisition. An organization can first tie the audit findings to these control families using the following steps:
- Review the audit findings and map them to the security control families.
- Calculate a risk score for each control family based on the total number of findings, the severity of the findings, and their collective impact.
- Sort the control families in the descending order of their risk scores.
While there are many methods for calculating the risk scores, the following example demonstrates one method.
Example:
There are six findings in the audit. These are first mapped to the control family. The severity (1–3) of each finding is noted along with its impact (1–10). The risk score for each finding is calculated using the following formula:
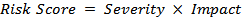
The risk scores for each control family are calculated by adding the individual risk scores for the findings mapped to it.
High-Risk Chart
| Control Family | Finding | Severity | Impact | Risk Score |
|---|---|---|---|---|
| Access Control | Finding #1 | High | 5 | 3 × 5 = 15 |
|
| Finding #2 | High | 4 | 3 × 4 = 12 |
| Total |
|
|
| 15 + 12 = 27 |
| Media Protection | Finding #3 | Medium | 6 | 2 × 6 = 12 |
|
| Finding #8 | Low | 3 | 2 × 3 = 6 |
| Total |
|
|
| 12 + 6 = 18 |
| Identification and Authentication | Finding #4 | High | 8 | 8 × 3 = 24 |
|
| Finding #5 | High | 7 | 7 × 3 = 21 |
|
| Finding #6 | High | 4 | 4 × 3 = 12 |
| Total |
|
|
| 24 + 21 + 12 = 57 |
From the above example it is clear that Identification and Authentication has the highest risk, followed by Access Control and then Media Protection.
Step 4: Establish Priority
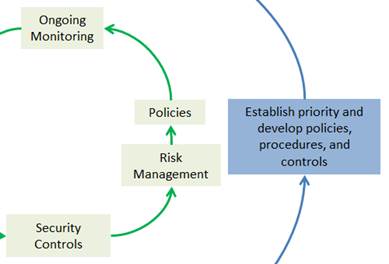
Once the risk has been determined, the organization can address the following elements of a security program:
- Security controls
- Risk management
- Policies
- Ongoing monitoring
Risk Management
The risk score provides the basis for prioritizing security controls. It has the following advantages:
- It gives the organization a good idea of the security areas in which it is lacking.
- It allows an organization to prioritize the implementation of the policies, procedures, and controls related to a control family.
The organization can now make an informed decision on which control family (families) to tackle first. The purpose for selecting a control family (or families) is to create policies and procedures and to implement formal controls to reduce the high level of risk. This risk-based approach allows an organization to address the most vulnerable security area(s) first.
Security Controls
NIST-800-53 provides guidance on the controls that need to be put in place for each control family. Some examples of security controls for the Access Control family (22 controls) are Remote Access, Wireless Access, and Access Control for Mobile Devices. The organization can choose specific controls from each family for implementation. These controls may address specific audit issues or be chosen as preventative measures.
Policies
Once the controls have been identified for implementation, the organization can concentrate on creating new policies and procedures specific for these controls or strengthen existing policies and procedures.
Ongoing Monitoring
The IT organization can also take this opportunity to establish ongoing monitoring to ensure that the controls being put in place are functioning as expected.
Benefits and Caveats
Following are some of the benefits of this approach.
Benefits
- The introduction of a common security framework for the organization promotes a common vocabulary and may improve communication.
- It provides a structured approach to gradually implement a security program.
- The program implementation is based on priorities derived from ground realities.
- It provides areas of focus to the organization for designing and implementing policies and procedures.
- It allows an organization to organically grow its security governance structure.
- Last but not least, the security program is strengthened with every audit cycle, and the approach provides a good basis for comparing past performance and measuring progress.
While there are benefits to the approach, there are also some caveats that need to be considered.
Caveats
- The implementation of the security program is based on current risks. The organization should also be mindful of future risks when putting controls in place.
- It is an iterative approach rather than a life-cycle approach to implementing a security program. There is no firm start date or end date to program implementation.
- The speed of program implementation may depend on the frequency of security audits.
Summary and Conclusion
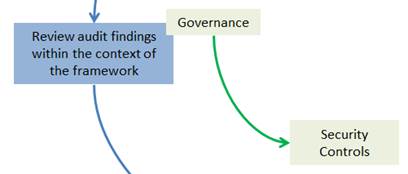
Higher education IT is charged with protecting the institution's information assets to comply with federal laws and regulations. Although organizations would like to put together a comprehensive security program as a proactive approach to avoiding security failures, lack of resources and competing priorities may prevent them from doing so. Given such circumstances, an organization can take an incremental approach to implementing a security program by choosing a framework/standard and using the security audit cycles to implement the program in a piecemeal manner. Choosing a security framework/standard allows the organization to introduce a common security vocabulary and improve communication of security-related issues. Figure 2 shows the approach as a whole and the possible effects on the different elements of a security program.
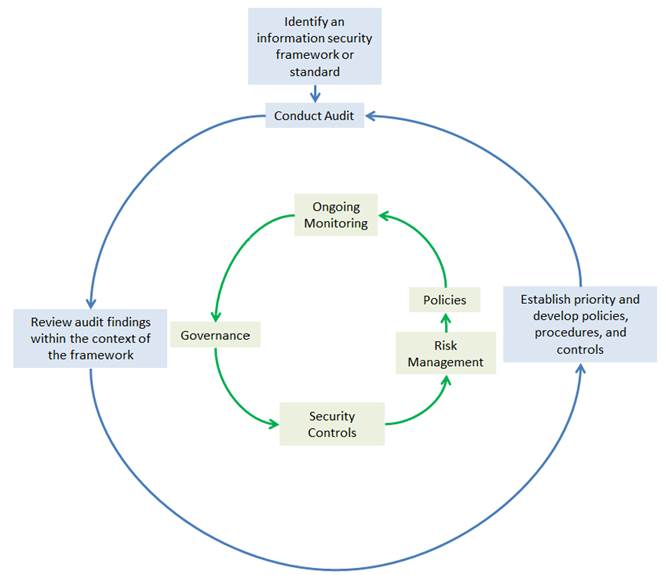
Figure 2. Overall approach and elements of a security program it may impact.
By reviewing its security audits within the context of a framework/standard, the IT organization can identify security areas that are at highest risk. This allows the organization to prioritize development of policies and procedures, implementation of security controls, and ongoing monitoring of the security program. The organization can slowly grow its security program and implement formal controls while addressing audit issues. With each iteration, the organization can formally track the improvements to its security program by comparing the risk levels with the previous cycles. This approach affords the IT organization the ability to control the pace at which its security program grows based on the availability of resources and personnel.
- See the NIST Special Publications (800 Series) website.
- See NIST-SP-800-53: Security and Privacy Controls for Federal Information Systems and Organizations and NIST–SP-800-100: Information Security Handbook: A Guide for Managers.
- Jan Van Bon, ITIL 2011 EDITION – A Pocket Guide (Van Haren Publishing, 2011).
© 2012 Pankaj Sharma. The text of this EDUCAUSE Review Online article is licensed under the Creative Commons Attribution 3.0 license.
